The WebsitePlanet research team in cooperation with Security Researcher Jeremiah Fowler discovered a non-password-protected database that contained over 61 million records belonging to users around the world. The massive amount of exposed records were related to IOT health and fitness tracking devices. Upon further investigation, there were multiple references to “GetHealth”, a New York City-based company that offers a unified solution to access health and wellness data from hundreds of wearables, medical devices, and apps.
I immediately sent a responsible disclosure notice of my findings and received a reply the following day thanking me for the notification and confirming that the exposed data had been secured.
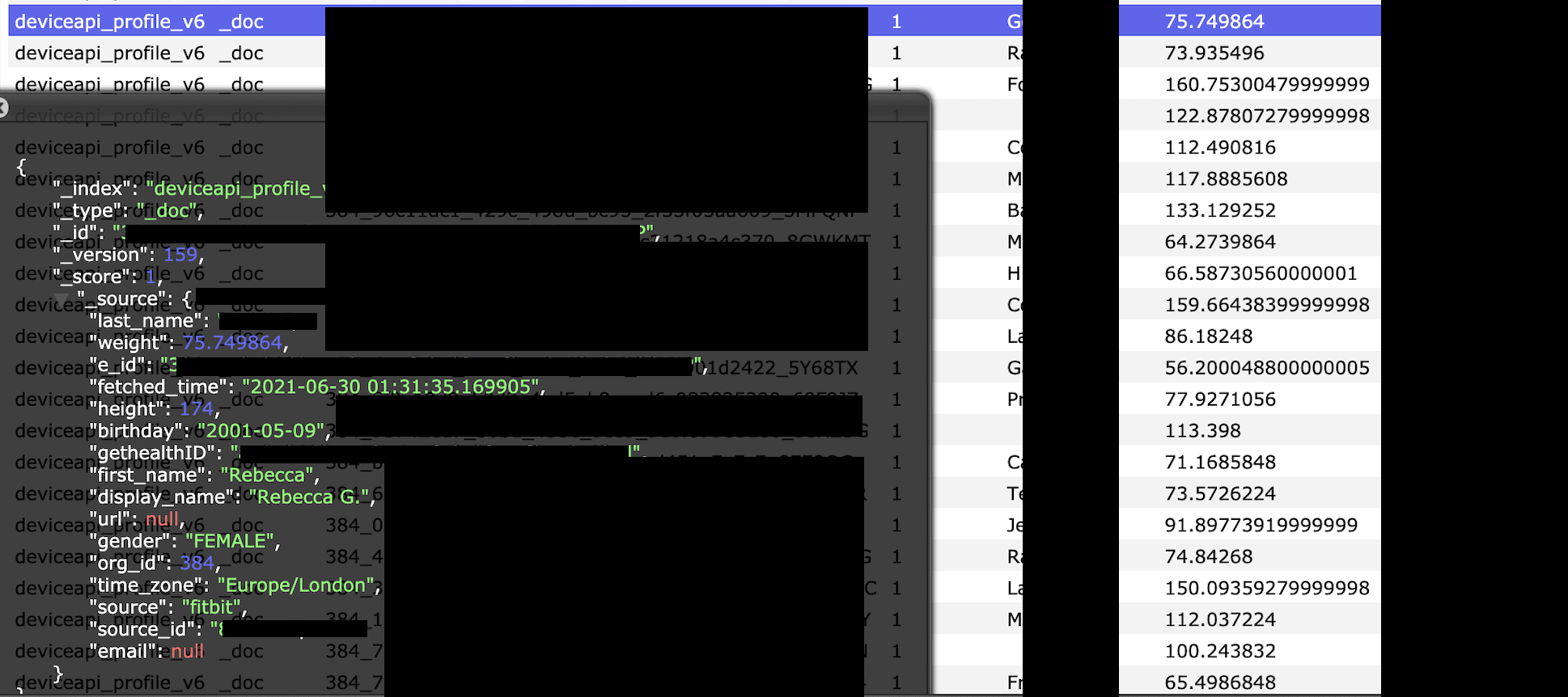
The most disturbing part of the discovery was that many of the records contained user data that included first and last name, display name, date of birth, weight, height, gender, geolocation, and more. This information was in plain text while there was an ID that appeared to be encrypted. The geolocation was structured as in “America/New_York”, “Europe/Dublin” and revealed that users were located all over the world.
In a limited sampling of 20k+ records some of the top wearable health and fitness trackers appeared as a “Source”. Fitbit (Purchased by Google for 2.1 Billion in 2021) appeared 2,766 times, instances of what appears to be Apple’s Healthkit 17,764. Other apps or devices may have also been affected. According to GetHealth’s website they can sync data from the following: 23andMe, Daily Mile, FatSecret, Fitbit, GoogleFit, Jawbone UP, Life Fitness, MapMyFitness, MapMyWalk, Microsoft, Misfit, Moves App, PredictBGL, Runkeeper, Sony Lifelog, Strava, VitaDock, Withings, Apple HealthKit, Android Sensor, S Health.
The Apple Healthkit can collect more complex metrics that include blood pressure, body weight, sleep levels, glucose, and more. Once an iPhone user gives permission to Apple’s health and fitness app it uses sensors in the phone, connected wearables, and smart devices to collect more health data than many of the other devices or applications. This operation can run silently in the background and on any iPhone that the user has given permission.
Here are the details of the findings:
- Total Size: 16.71 GB / Total Records: 61,053,956
- Exposed Indices:
- deviceapi_fitness
- deviceapi_heartrate
- deviceapi_profile
- deviceapi_pulseox
- deviceapi_sleep
- deviceapi_speed
- deviceapi_tracker
- deviceapi_weight
- Internal records that expose the following: deviceapi_profile, type, id, score, source, source_id, weight, e_id, fetched_time, height, birthday, gethealthID, first_name, last_name, display_name, url, gender, org_id, time_zone.
- This information could be used in a targeted phishing attack or to obtain additional health information about users.
- The files also show where data is stored and a blueprint of how the network operates from the backend and was configured.
Example of how user data appeared in the database:
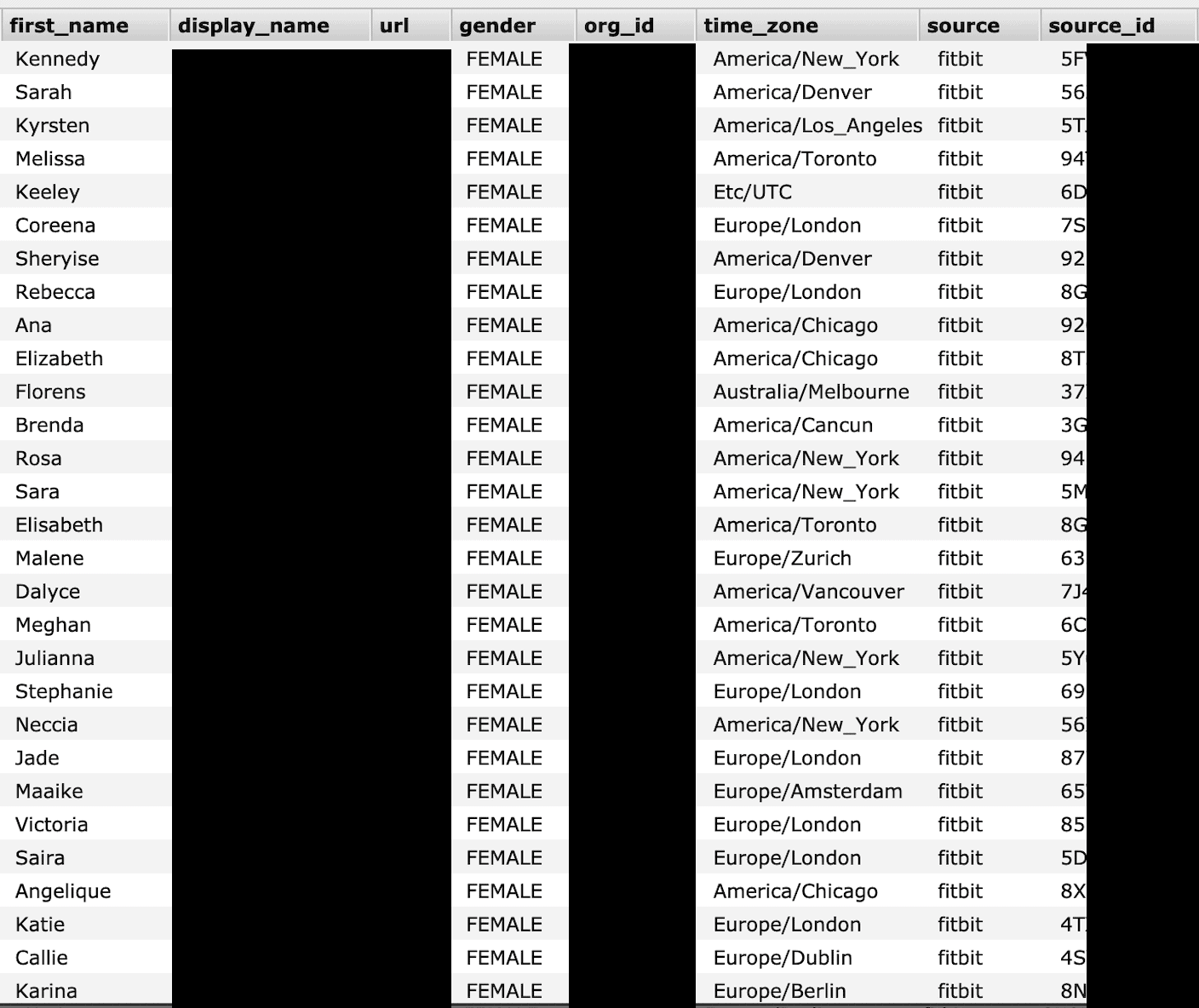
Example of a Profile Account:
Fitness Trackers Pose Privacy Risks
Fitness trackers by their design are intended to understand and improve our health by providing critical information that could indicate health risks. In the process of collecting this information on users, the device must be able to access very private information about our lives, health, and much more.
According to a report conducted by the Pew Research Center, an estimated 20 percent of adults in the United Stated report owning some type of wearable device or fitness tracker. These devices will produce a massive amount of health-related data points over the years and create long-term privacy risks.
Many of these devices are not anonymous and tied to user accounts where they are encouraged to input personally identifiable information in their profile. This could make it extremely easy to identify who the data belongs to in the event of a data breach. Another problem is that there are no uniform privacy standards for wearables and there is a potential for companies to use this data for advertising, marketing, or sharing with 3rd parties. Another consideration is how companies will offer users an “end of use policy” and how long this data will be stored?
What is considered a Medical Device?
Wearables Pose Complex Questions
There is some debate over how wearable and fitness trackers or IOT wearables can be considered medical devices. The line between an application that has a medical purpose is becoming increasingly blurred. In recent years regulatory agencies in the UK, US, and EU have tried to define what is a medical device and how they should be regulated. This information is very valuable for medical research and the health and wellness industry.
The Food and Drug Administration designated FitBit as a software for over-the-counter use and a Class II medical device. On September 14, 2020 Fitbit received FDA clearance and CE mark approval for its electrocardiogram function to track heart rhythm irregularities. Fitbit’s devices now collect data on an estimated 29 million users worldwide and Google claims that Fitbit users’ health and wellness data won’t be used for Google ads. In many other sectors the technology outpaces the laws and regulations at the expense of users’ privacy.
According to Gethealth.io’s website and FAQ the process is HIPAA compliant and states “users’ data is secure with SSL transport, AES256 encryption, logging, and monitoring and all data is stored and managed in a HIPAA compliant way.”
The Health Insurance Portability and Accountability Act of 1996 (HIPAA) is a US federal law that protects sensitive patient health information from being disclosed without the patient’s consent or knowledge. There are currently no clear HIPAA regulations that apply to wearable technology as long as the data is used for personal use. However, once the data from a wearable technology is passed to a healthcare provider or other institution it may then be subjected to HIPAA regulations and HIPAA compliance standards. Wearable devices and smartphones have the technology to collect Patient Generated Health Data (PGHD) that could expose sensitive health data, but the regulation seems to be far behind.
Most wearable users think that no cybercriminal is interested in how many steps they take or how long they sleep, but this is a mistake to ignore how your data is used or shared. All data is valuable and as the technology of wearables expands, so does the types and accuracy of data that is collected on users. A simple step counter or pedometer is relatively harmless, while some wearable devices can identify more detailed information such as your heart rate or body mass index and much more. In theory the detailed information that fitness trackers collect on millions of users can provide an overall portrait of these individuals and their general health. This data could then be used to carry out other attacks, fraud, extortion, or to obtain more targeted health information.
Collecting and Storing Health Data is Risky
All of the information that is collected must be stored somewhere and this creates a vulnerability and a point of a potential data exposure. The healthcare industry needs data management platforms to collect and filter the high volume of data they collect. The global health management market is expected to grow to as much as US $46.7 billion by 2026. As the healthcare technology industry grows so does the amount of data being collected and stored.
Health data from wearable devices is a treasure trove of information and will undoubtedly become a target for cybercriminals. It is a well-known fact that the health industry experiences more data breaches than any other sector. According to a report conducted by Trustwave, healthcare data can sell for up to $250 per record on the black market or dark web. That is a considerable sum compared to credit card records that are valued at an estimated $5.40.
It is unclear how long these records were exposed or who else may have had access to the dataset. As security researchers, we never extract or download the data we find and only take a limited number of screenshots for validation purposes. We are not implying any wrongdoing by Gethealth, their customers or partners. Nor, are we implying that any customer or user data was at risk. We were unable to determine the exact number of affected individuals before the database was restricted from public access. We are only highlighting our discovery to raise awareness of the dangers and cyber security vulnerabilities posed by IOT, wearable devices, fitness and health trackers, and how that data is stored. We advise any company or organization to encrypt sensitive data, enact cyber hygiene practices, and conduct penetration testing often.







